The digital landscape is constantly evolving, and a significant shift is the trend towards shorter-lived internet certificates. With proposals from Google and Apple to dramatically reduce certificate lifespans, the traditional manual approach to certificate management is becoming unsustainable. Shorter validity periods enhance reliability, but this necessitates a robust automation strategy. This is where the Automated Certificate Management Environment (ACME) protocol, specifically ACMEv2, offers a powerful solution.
Understanding ACMEv2
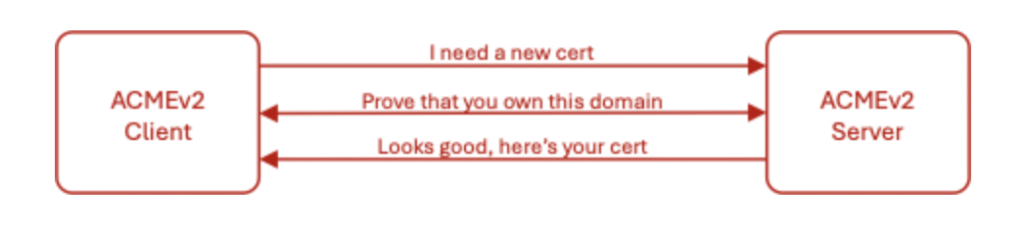
At its core, certificate automation via ACMEv2 involves three steps:
- Requesting a certificate from a Certificate Authority (CA).
- Satisfying a challenge to prove domain ownership.
- Retrieving and installing the new certificate.
The most common challenge type is http-01, where the ACME server sends a unique token to the client, which then places this token on the HTTP server at a specific URL for verification. Upon successful validation, the certificate is issued.
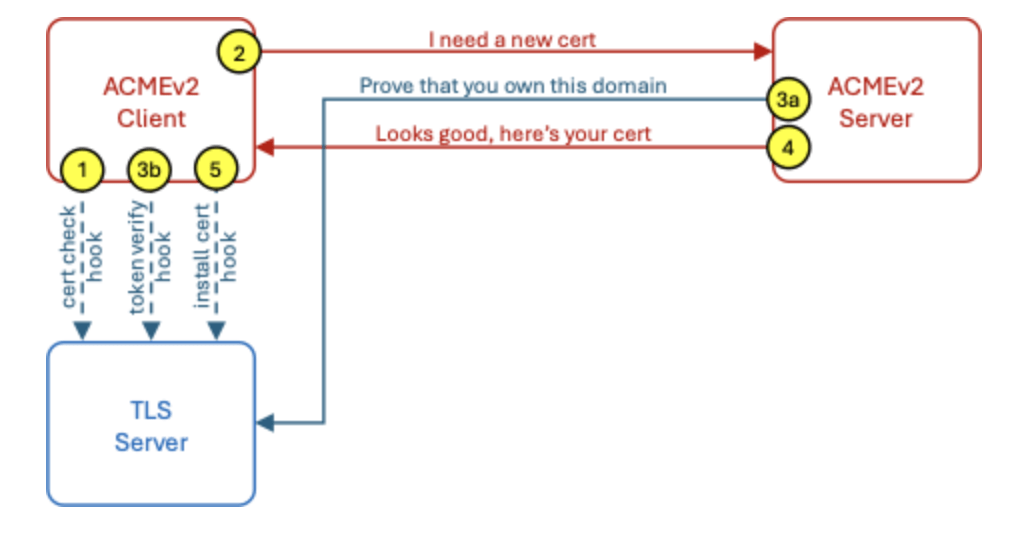
I’ve been using DNS-01 in my environment.
Beyond http-01: The dns-01 Challenge
While http-01 is widely used, the dns-01 challenge offers an alternative, especially when an HTTP:80 listener on the public internet isn’t feasible. This is often relevant for BIG-IP management device certificates. However, directly automating management device certificate renewal via ACMEv2 is generally not practical due to security considerations. For management certificates, alternatives include managing them as traffic certificates and then moving them to the device with a script, or hosting an internal ACMEv2 service with dns-01 validation. The EST (Enrollment over Secure Transport) protocol is also a more secure and suitable alternative for automating management certificate renewals, particularly within internal PKI environments.