Recently, while attempting to expose a Kubernetes workload in my cluster using the Tailscale Kubernetes Operator and a Tailscale-powered LoadBalancer Service, I ran into a pretty interesting issue that’s common for users on OpenShift or environments with strict security context constraints (SCCs).
The Problem
After deploying the Tailscale Operator and configuring my workload, I noticed my LoadBalancer Service wasn’t getting assigned a Tailscale hostname. Checking the Service status, I saw:
no Tailscale hostname known yet, waiting for proxy pod to finish auth
Digging further into the events, the more revealing error was:
create Pod ts-nginx-frontend-service-xxxx-0 in StatefulSet ts-nginx-frontend-service-xxxx failed error:
pods "ts-nginx-frontend-service-xxxx-0" is forbidden: unable to validate against any security context constraint:
[provider "anyuid": Forbidden: not usable by user or serviceaccount,
provider restricted-v2: .initContainers[0].privileged: Invalid value: true: Privileged containers are not allowed,
...
provider "privileged": Forbidden: not usable by user or serviceaccount]
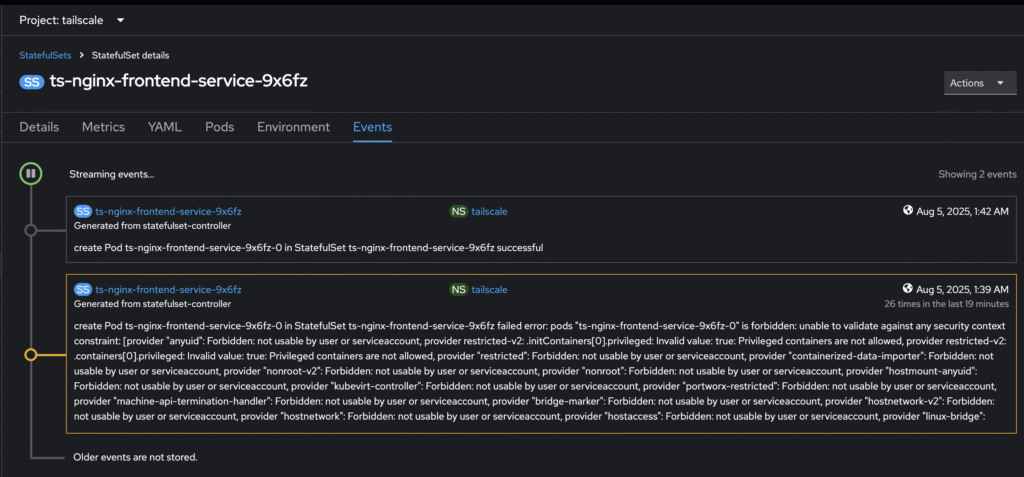
This essentially meant the Tailscale proxy pod tried to start with privileged permissions, but none of the SCCs assigned to my ServiceAccount (“proxies” in the “tailscale” namespace) allowed this. OpenShift, by design, blocks privileged pods unless specifically allowed.
The Solution
After a quick review, the fix was straightforward: I needed to grant the privileged SCC to the ServiceAccount my Tailscale proxy pods use. This was very similar to the earlier post I had where I had to grant scc to the ServiceAccount operator so that the pod can deploy smoothly with it’s needed permissions.
Here’s the exact command that resolved the issue for me:
oc adm policy add-scc-to-user privileged -z proxies -n tailscaleThis command associates the privileged SCC with the proxies ServiceAccount in the tailscale namespace, allowing the Tailscale proxy pods to run with the needed permissions. Soon after, the proxy pods started successfully, and my LoadBalancer Service got its Tailscale hostname and became reachable as intended; take note it is not able to respond to ICMP. If you need SSL/TLS, you’ll need to expose it via Ingress resource.
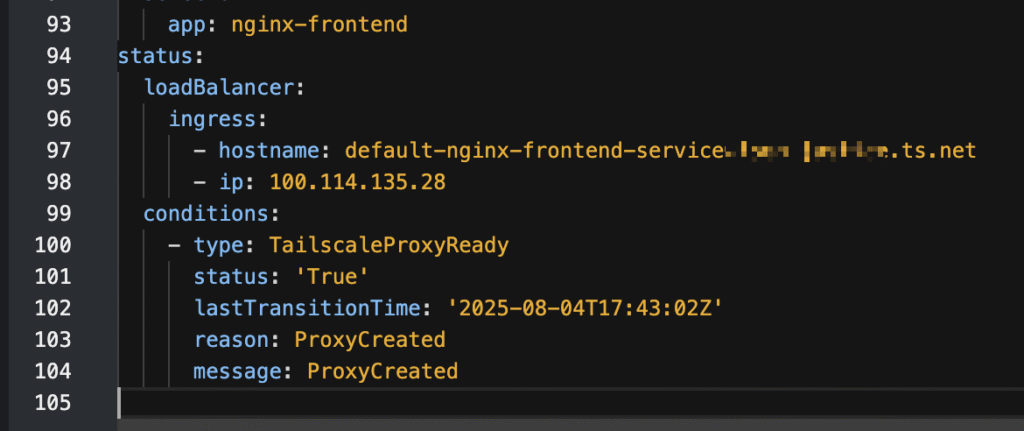
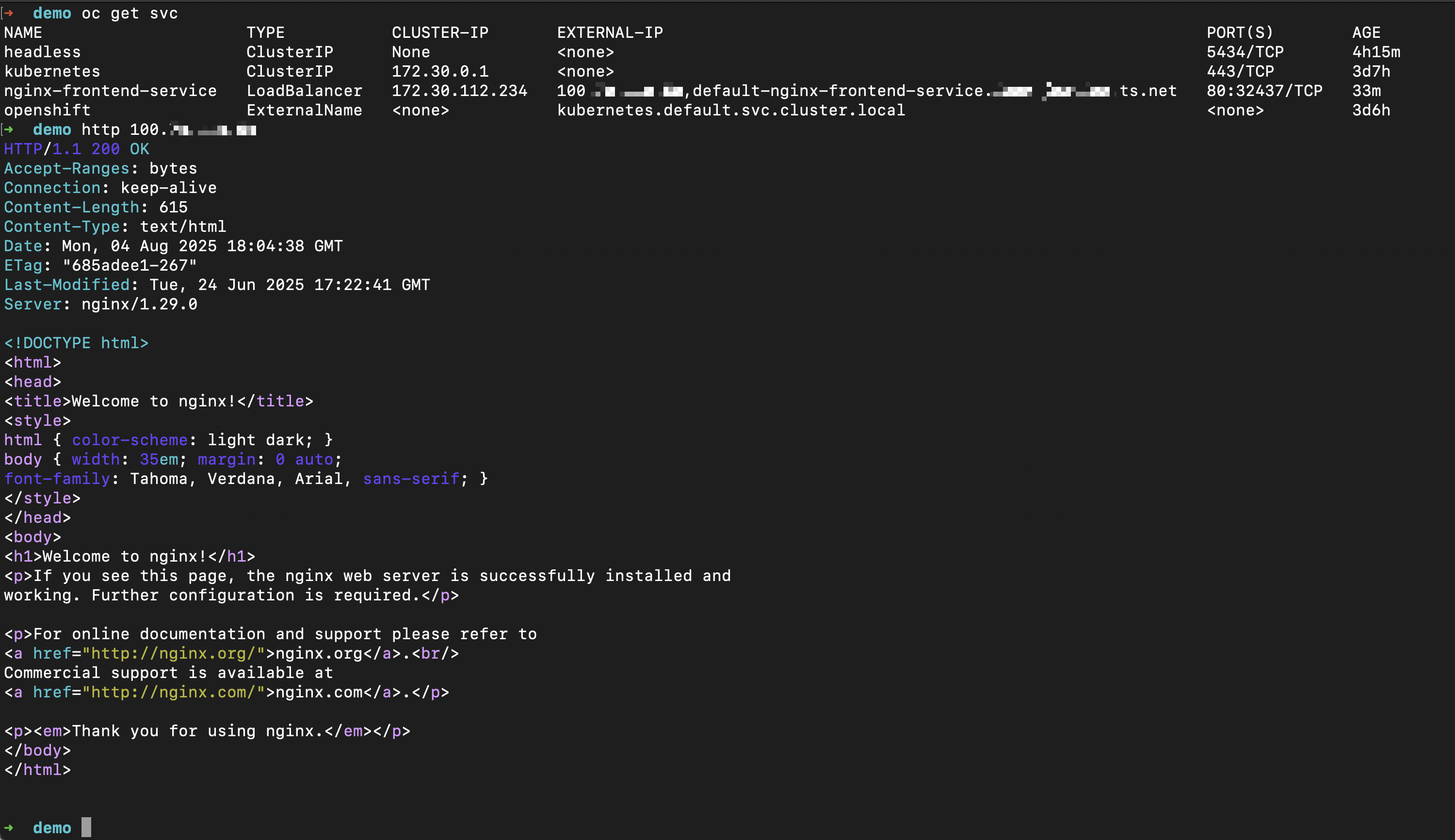
See below screenshots, I am getting external IP and FQDN from tailscale.
Key Takeaways
- If your Tailscale load balancer service is stuck “waiting for proxy pod to finish auth” on OpenShift, check if your proxy pods are failing due to SCC restrictions.
- Granting the
privilegedSCC to your ServiceAccount (withoc adm policy add-scc-to-user privileged -z <serviceaccount> -n <namespace>) is usually necessary for network plugins or operators needing additional privileges. - Always review and limit SCC privileges to only those ServiceAccounts that require them for security.
Hopefully, this saves you the time I spent debugging!
oc adm policy add-scc-to-user anyuid -z operator -n tailscale